

Our Cybersecurity consulting services encompass the strategic, operational, and technical dimensions of security. They involve creating robust security programs for the future and incorporating specialized controls and technologies. These actions are designed to effectively address vulnerabilities in software and IT infrastructure, identifying and thwarting intrusion attempts. Following are some of the services we offer
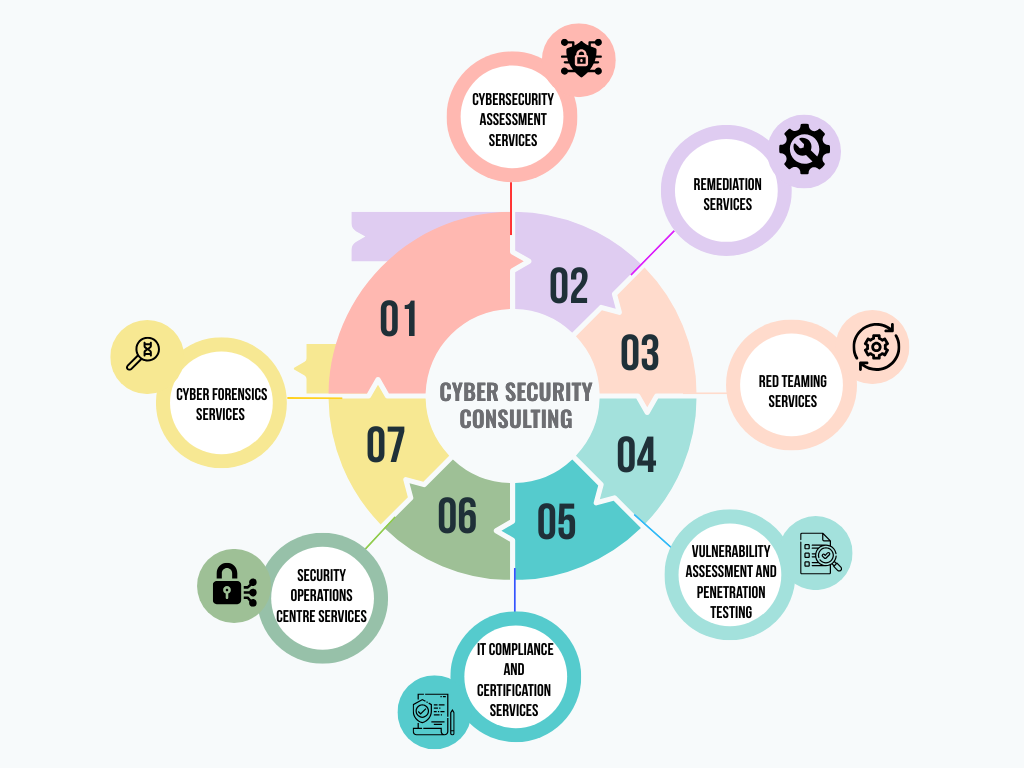
Cybersecurity assessment services involve evaluating and enhancing the security posture of an organization's digital infrastructure, systems, and data. Here's an overview of key aspects of cybersecurity assessment services:
Remediation services in the context of cybersecurity involve addressing and mitigating identified vulnerabilities, weaknesses, or issues identified during assessments or security incidents. Here's an overview of key aspects of remediation services
Red teaming services play a crucial role in helping organizations identify and address security weaknesses proactively. By simulating real-world threats, red teaming provides a comprehensive understanding of an. Here's an overview of key aspects of red teaming services
Vulnerability Assessment and Penetration Testing (VAPT) services are crucial for identifying and addressing security vulnerabilities within an organization's systems and networks. Here's an overview of key aspects of VAPT services
IT compliance and certification services are crucial for ensuring that an organization's Information Technology (IT) practices align with industry standards, regulations, and best practices. Here's an overview of key aspects related to IT compliance and certification services
Security Operations Centre (SOC) services play a crucial role in proactively monitoring, detecting, and responding to cybersecurity threats within an organization. Here's an overview of key aspects related to SOC services
Cyberforensics
services, also known as digital forensics or cyber forensic
analysis, involve the investigation and analysis of digital evidence to uncover and
understand cybersecurity incidents, data breaches, or cybercrimes while preserving the
integrity of digital evidence for potential legal proceedings.
Here's an overview of key aspects related to CyberForensics services

 Helpdesk
Helpdesk
Loading...